【新唐人2011年9月22日訊】日本最大國防承包商「三菱重工」遭遇網路駭客攻擊,引發日本國內高度關注,日本媒體報導指出,攻擊的病毒當中包含有中文簡體字。請看報導:
《朝日新聞》等日本媒體20號報導,8月,「三菱重工」旗下的長崎造船所、神戶造船所、愛知縣小牧市的名古屋誘導推進系統製作所等,11個工廠和研究所的伺服器、電腦共83臺確認感染電腦病毒。病毒包含會竊取電腦信息的「特洛伊木馬」,有證據顯示,被感染的電腦自動跟中國等地的海外服務器連接,某些信息可能洩漏。
報導說,這些工廠和研究所主要負責研發潛艇、導彈防禦系統以及核電廠零件,儲存了大量日本尖端軍事科技文件。
日本主要報紙《讀賣新聞》,20號下午發表了一篇 「攻擊三菱重工服務器、病毒當中包含中文簡體字」的報導文章。
報導說,「被感染的電腦被攻擊者遙控,而遙控電腦畫面顯示使用的是中文。由於可能牽涉嫻熟中文的人參與攻擊行動,警視廳認為,這有可能是國際性的間諜事件,決定以涉嫌違反禁止不正當進入電腦系統的法律為理由展開調查。......有關官員表示,電腦信息安全公司對有關的電腦病毒進行分析,發現攻擊者使用外部的電腦進行操作,畫面上有中國大陸使用的簡體漢字。」
除「三菱重工」以外,造船和重型機械大公司IHI(舊稱『石川島播磨重工業』)20號也表示,過去曾接到附加病毒的電子郵件。另外,從事戰鬥機製造等防衛產業的「川崎重工」20號也說,有人向公司多次發送被認為是用於網絡服務器攻擊的電子郵件。
另據日本警視廳公布,人事院和內閣府等政府機關管理的主頁,在9月17號晚到18號晚受到「分散式拒絕服務(DDoS)」攻擊,短時間內有大量數據同時湧入,一度無法正常瀏覽。
《讀賣新聞》的報導還說,中國國內網站從9月12號開始,出現呼籲在「9•18事變」80週年,對日本發動網絡攻擊的留言,並公布了日本警視廳,人事院等約10個政府機關網址,其中還有具體教授如何使用攻擊軟件的貼子。
此外,福岡縣部分民間機構網站也在同一時間遭到攻擊,頁面內容被改寫為中文。日本相關政府機構的網站去年9月及今年7月也曾遭到攻擊,兩次的攻擊者IP地址有九成來自中國。
據網絡安全專家發佈的監測結果,近5年,包括聯合國和國際奧委會在內的全球70多個機構,都成為駭客攻擊的目標,其中一半以上機構都在美國。電腦安全公司邁克菲認為,攻擊「可能來自某國政府」,《華盛頓郵報》則直接道出:這些駭客攻擊似乎起源於中國。
針對外界指責中共駭客攻擊國外網站,中共當局一貫給予否認。不過近期,中共媒體《央視》的軍事科技欄目,無意洩露了中共軍校研髮網絡攻擊系統,有針對性的攻擊美國法輪功網站的實情,給他國針對中共網絡攻擊的調查留下了證據和參考。
《日本經濟新聞》21號發表社論,呼籲對威脅國家安全的伺服器攻擊做好準備。報導說,涉及國家機密的企業和機關受到來自海外的攻擊,應該深切認識到它的危險性,立即準備對應攻擊的體制。
新唐人記者尚燕、孫寧綜合報導。
Cyber-attack On Mitsubishi, China Suspected
Japan's largest defense contractor,
Mitsubishi Heavy Industries, Ltd., was subjected to cyber-attacks,
causing public alarm.
Japanese media reported that the virus contains
simplified Chinese characters. Here is the report:
Asahi Shimbun and other Japanese media reported on August 20
that a total of 83 virus-infected computers were found at 11 manufacturing, research, and development sites,
including Nagasaki Shipyard & Machinery Works, Kobe Shipyard
& Machinery Works, and Nagoya Guidance & Propulsion System.
The types of computer viruses found include Trojan horses.
There is evidence that indicates that the infected computers
automatically connected to servers located in countries such as China.
Some information may have been leaked.
The paper said that although these companies build submarines,
guided missiles, and nuclear power stations,
they also store documents containing key military
and technology of Japan.
A major Japanese newspaper, Yomiuri Shimbun, published
an article titled, “Simplified Chinese Used in MHI Cyber-attack,” in the evening edition, on Sept. 20..
The report said, “Simplified Chinese characters were used
by attackers to remotely control the infected PCs.
The Metropolitan Police Department (MPD) now considers this
an international espionage case, as it is believed that those involved had a thorough knowledge of the Chinese language.
The MPD is investigating the case as a violation of the law
on the Prohibition of Unauthorized Computer Access.
An information security firm that copied and
analyzed the virus discovered the simplified Chinese characters on screens used by the senders.”
In addition to Mitsubishi Heavy Industries,
IHI (Ishikawajima-Harima Heavy Industries), which supplies engine parts for containment vessels and
pressurized vessels for nuclear reactors, also reported that
they were victims of a cyber-attack on the Sept. 20.
Kawasaki Heavy Industries, which makes airplanes and
rocket systems, has also been subjected to virus-tainted emails, according to a company spokesman.
The Japan National Police Agency said that websites belonging to
the National Personnel Authority and Cabinet Office,
and others, came under cyber-attack on the evenings of
Sept. 17 and 18, experiencing a so-called Distributed Denial-of-Service (DDoS) attack in which
hackers send a massive amount of data to a targeted website,
overwhelming its ability to respond or function properly.
Yomiuri Shimbun also reported that since Sept. 12, some
Chinese websites are calling for cyber-attacks against
Japanese websites—to mark the 80th anniversary of
the 1931 Manchurian Incident.
Among the proposed targets in Japan, are 10 Japanese
government agency websites, including the Japanese National Police Agency and the National Personnel Authority.
The Chinese websites also provide complete instructions on
how to launch viral-laden software.
At the same time, some private sector websites in Fukuoka
Prefecture also came under cyber-attack, with some web-page content being rewritten in Chinese.
Some Japanese government websites were also attacked
during last September and this past July.
Ninety percent of the attacker IP addresses
have been traced to China.
According to an investigative report released by security experts,
more than 70 institutes world-wide have become targets of hackers in the past five years,
including the United Nations and the International Olympic
Committee, with more than half of agencies located in the United States.
In its report, security firm, McAfee, said the large-scale
cyber-espionage operation was conducted by a "state actor,"
whereas the Washington Post bluntly stated that
“these hackers seem to have originated in China.”
While the Communist regime has routinely denied their
involvement in the cyber-attacks in the international community,
recently, the regime』s state-run media, CCTV,
unintentionally leaked, during one of its programs, evidence
that a Chinese military university is engaged in
cyber-warfare against Falun Gong websites in the United States.
This has provided evidence proving that the Communist regime』s
does engage in cyber-attacks on other countries.
Japan』s Nikkei (Japanese Economic News) editorial commented
on the Sept. 21 that the nation needs to be prepared for cyber-attacks that threaten national security.
The report noted the seriousness of such attacks saying that
when companies and institutions that involve state secrets receive
attacks from overseas, an anti-cyber-attack system
should be immediately deployed.
NTD reporters: Shang Yan and Sun Ning
看下一集

【禁聞論壇】中國式次貸危機即將發生?
【禁言博客】卡扎菲政權的倒臺告訴世界甚麼?

【禁聞】美臺軍售案 中共反應烈

【禁聞】《央視》將改版 民眾:改也不看
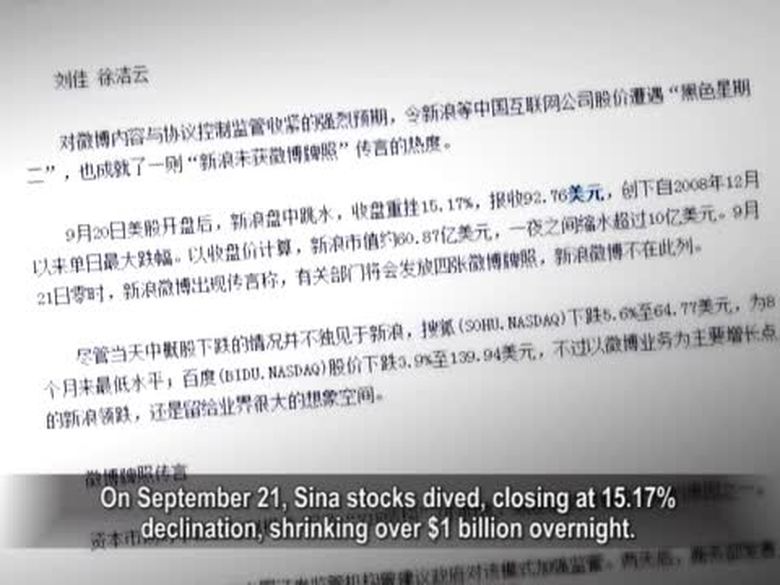
【禁聞】新浪遇“牌照門” 再陷“關閉門”
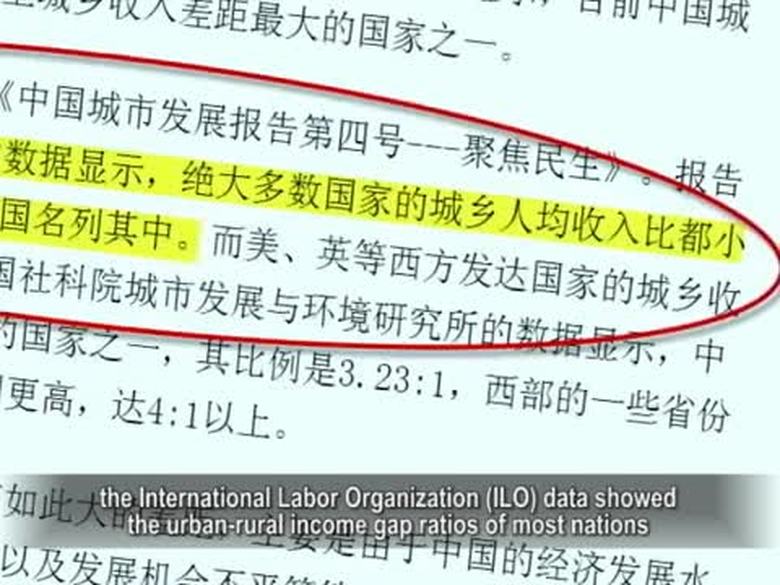
【禁聞】報告:中國城鄉差距世界第一

【禁聞】李明博紐約領獎 遣返法輪功受譴責

【禁聞】京城兩報遭貶 整肅背後內幕
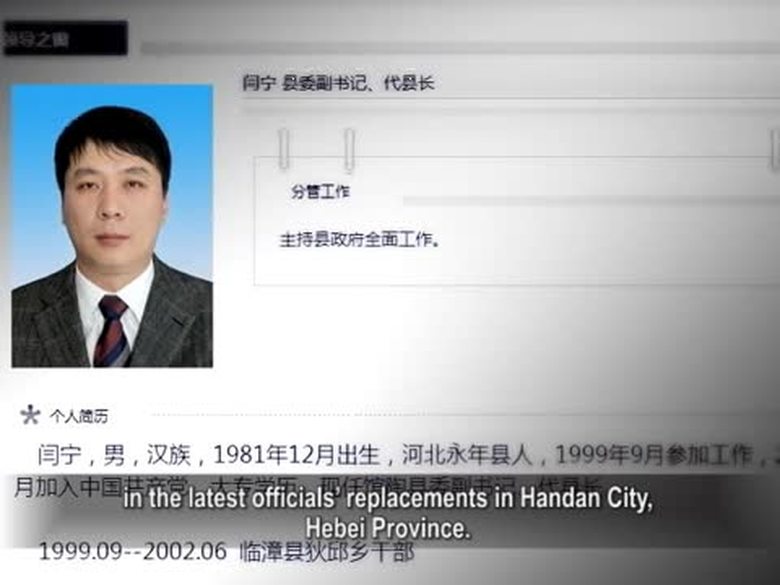
【禁聞】29歲縣長 又一場“拼爹遊戲”?
【禁聞】紅衛兵要平反 既受害又害人
【禁聞】駁稅負痛苦指數全球第二 黨報挨批

【禁聞】批美大使 《環球時報》「施暴」

【禁聞】高牆裏的故事:溫柔遭遇暴力

【禁聞】4200億元和高利貸泡沫的隱憂

【禁聞】烏坎村抗爭未完 龍頭村再揭竿起義
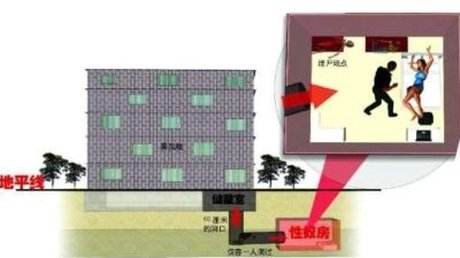
【禁聞】洛陽性奴案也成「國家機密」?








